Finding the right alignment of your people, processes, and technology can be a challenge. For corporate leaders, assuming that your operations are in ship shape can easily turn into an unwanted risk. This is where the Physical Security Ecosystem comes in.
The physical security ecosystem is a method to align people, processes, and technology against operational activities. Together with a comprehensive risk management plan and strategy, the physical security ecosystem method reveals how corporate leaders can establish a central source of the truth.
The Central Source of Truth is at the Heart of the Physical Security Ecosystem
Unlike other frameworks used to help align processes, the physical security ecosystem method breaks down visibility and control – two areas that are often missing or limited in an operation – into an actionable system of processes that help to control your security operations, using people process and technology to drive that level of control.
The Physical Security Ecosystem Introductory Guide
The ecosystem works to establish the central source of truth by allowing for each element to connect seamlessly. This seamless connection works like a puzzle piece and interlocks with one another to form the central source of truth at its core.
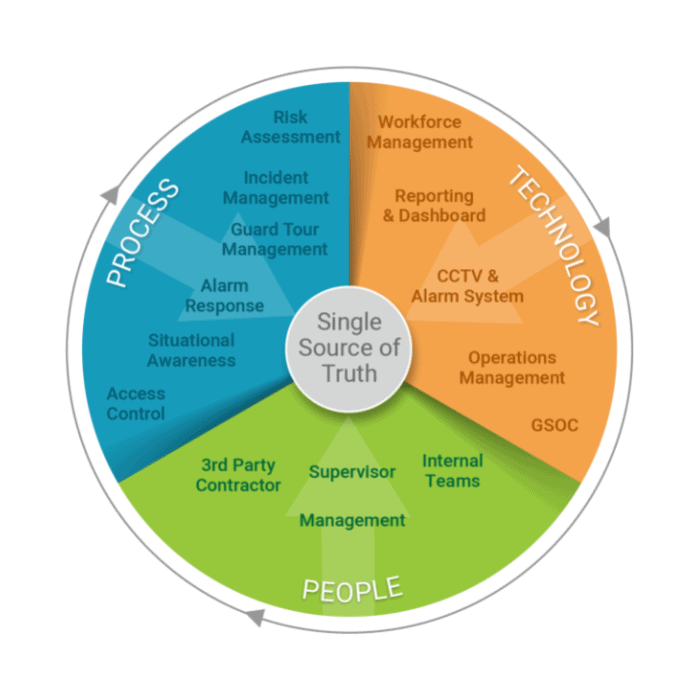
The 3 Elements that Define the Physical Security Ecosystem
You’ve probably heard the phrase of late “single source of the truth.” It’s catchy and yet thrown out there to explain just about anything related to technology use. The true meaning of a “single source of the truth” is the idea that truth lies in unity of processes. This means operational convergence and fluidity that allows for streamlined operations and communications.
Without a single source of the truth, corporate leaders gain only partial information – limiting visibility – and put at risk the value of their operations – relinquishing control. Aligning people, processes, and technology helps leaders get back that missing visibility and control.
- Aligning People: Aligning your people ensures that the safety and security of internal and external teams, organizational staff, and organizational operation alway remain a priority.
- Aligning Processes: The right processes in place enables your people to maximize the level of visibility and control possible to achieve operational excellence.
- Aligning Technology: Technology helps create the automation, the collaboration, and the integration of processes and people to ensure that you are getting the most efficiency within your operation.
Getting Started with the Physical Security Ecosystem: A Two Step Approach
Reassess the Overall Health of Your Operations
The pandemic revealed many inconsistencies in operations, team communications, and the overall health in corporate leaders’ operations. In a recent State Of Corporate Security Survey, nearly 93% of corporate leaders shifted their priorities to meet or exceed adaptability pressures brought on by the pandemic. This resulted in leaders reassessing their operations and revamping their risk management plans and strategies.
Enhance Your Team’s Training and Education
The key to upholding the ecosystem is ingrained value in how each element works throughout the organization. Proper training will unify your team on how to adhere to these processes and can simplify the use of technology to ensure each element of the ecosystem is followed. This would include:
- Enhanced communication practices giving rise to trust among security personnel and operational staff;
- Education on operational processes and a redefinition of the role security plays in minimizing risk
- An understanding of how technology, and its proper use, can minimize communication, eliminate team silos, and provide a centralized view of operations
Avoiding Third-Party Disruption to the Physical Security Ecosystem
While the rise in supplementing security officers with external resources, such as contract security, isn’t stopping, it can greatly impact the visibility component to a leader’s operations.
In short, if contract security utilizes their own technology options, and insist on using their tools and processes to fulfill their contract obligations, then a chasm in the ecosystem prevents a true single source of visibility – increasing risk and potential breaches to proprietary information.
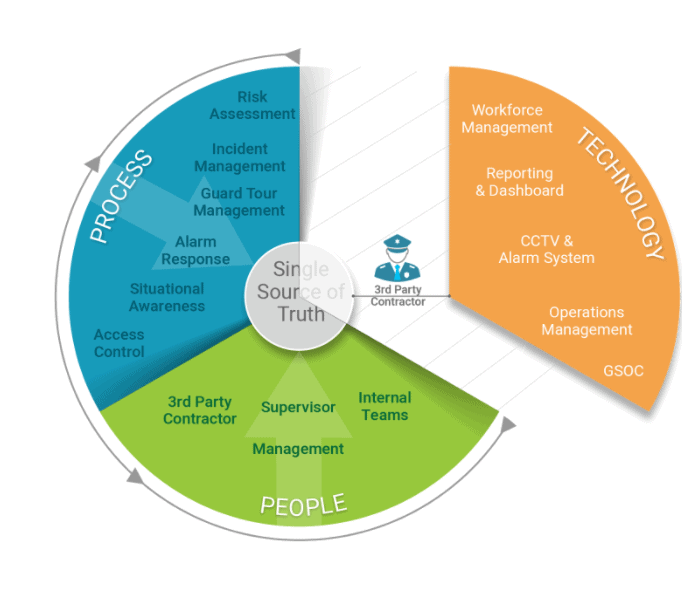
Corporate leaders can take charge of their organization’s information while maintaining the ecosystem by ensuring the ownership of technology. As part of any long-term strategy for the organization’s security, corporate leaders can require security firms to adhere to the tools and processes outlined in the organization’s security plan.
Establishing the Full Circle
While the physical security ecosystem method is a relatively new concept, in its core is a familiar stance – unifying a process is the only way to achieve true visibility and operational control. In using the ecosystem method, corporate leaders can approach their operations with peace-of-mind knowing that their team is upholding a holistic view of security.



