The lines between physical and digital security are increasingly blurred. Organizations have invested heavily in cybersecurity, with spending reaching $188 billion, according to recent data. However, physical security, which has received just $124 billion, remains a significant and often overlooked challenge.
This imbalance creates vulnerabilities that attackers can exploit. Organizations can build a more robust defense against data breaches and cyber threats by integrating physical and digital security measures. Let’s explore this further.
Physical Security Lapses Lead to Data Breaches
A study by Shred-It and the Ponemon Institute points out a stark reality: lapses in physical security can lead to significant data breaches.
A report from Security Intelligence reveals that 10% of malicious data breaches were attributed to physical security compromises. Specific incidents included:
- Unauthorized access to server rooms
- Critical data centers left unprotected can be easily exploited
- Theft or damage of servers
- Physical theft disrupts operations and allows attackers to extract data
- Installation of rogue devices
- Unauthorized devices can be used to infiltrate networks
That’s not all. As Security Today points out, the increasing adoption of IoT and complex industrial devices requires a more integrated approach to security. Interconnected cyber-physical systems expand the attack surface, making it easier for physical security oversights to result in data breaches.
Several common physical security threats often lead to data breaches:
- Unaccounted visitors: Monitoring and controlling visitor access to secure areas is important.
- Theft of documents and devices: Implementing secure storage solutions can prevent unauthorized access to sensitive information.
- Social engineering tactics: Training employees to recognize and counteract impersonation attempts can thwart many social engineering attacks.
- Tailgating: Ensuring that only authorized personnel can access secure areas can prevent unauthorized entry.
The Evolving Role of Security Guards in Cybersecurity
As organizations adopt more interconnected systems and advanced technologies, the role of security guards becomes critical in preventing physical and digital breaches. While traditional security measures like verifying identification and managing entry points are essential, modern security guards must also be equipped with the knowledge and tools to combat cyber threats from physical security lapses.
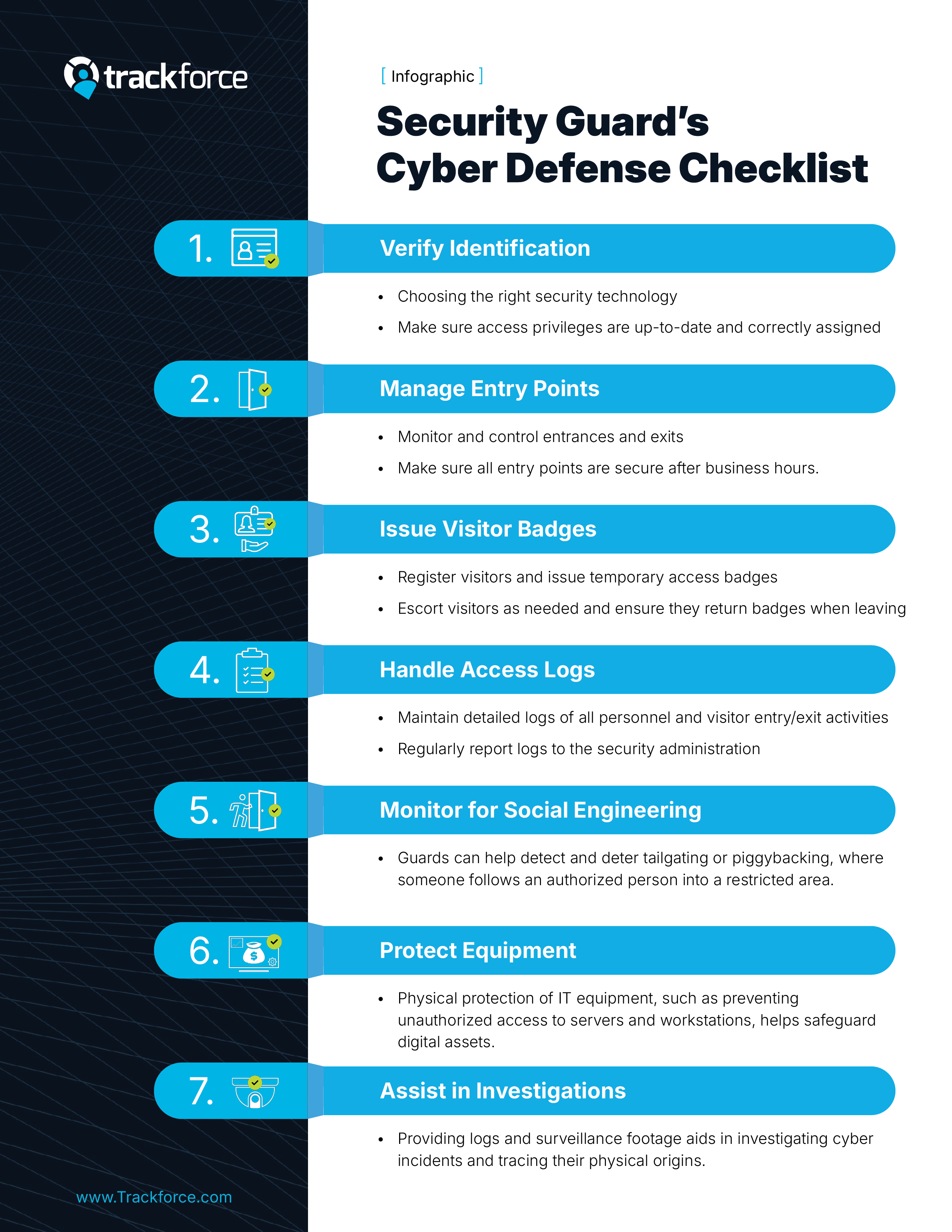
This is why training guards on new cybersecurity prevention measures is so critical. By incorporating these measures into their daily routines, guards can help fortify the digital fortress and protect the organization’s valuable information assets. Below is an essential checklist to guide security guards in preventing cybersecurity breaches:
Advantages of Combining Security Functions
What does an integrated security approach look like, and how can workforce management solutions from Trackforce help? Let’s look at the components of an integrated security approach.
- Unified security policies and protocols: Comprehensive policies addressing physical and cybersecurity threats are important. These policies must be consistently enforced across all departments to ensure everyone is on the same page.
- Centralized monitoring and management: Platforms that offer centralized management of security operations are helpful. Real-time monitoring tools provide oversight of both physical access points and digital networks.
- Access control and visitor management: Sophisticated access control systems manage who enters and exits secured areas. Integrated visitor management systems track and log all entries, clearly showing any onsite activity.
- Training and awareness programs: Regular training educates about the importance of integrated security. Awareness programs highlight common security threats and best practices for reducing risk.
- Incident response and recovery: Practiced incident response plans are helpful for both physical breaches and cyberattacks. Rapid recovery protocols minimize data loss in the event of an incident.
How Trackforce can help
Trackforce offers workforce management software solutions that enhance security operations and situational awareness. These tools are essential for developing an integrated security approach. Here are six key benefits:
1. Real-time incident reporting and management
These platforms allow for the creation of an immediate incident report, which allows for a quick response and resolution. Detailed logging helps with incident tracking, trend analysis, and efficient reporting.
2. Communication and coordination
Real-time alerts and notifications keep security teams informed about incidents as they happen, helping with better coordination and faster responses. Integrated communication tools help connect people across different locations.
3. Patrol management and tracking
Patrol scheduling helps with regular monitoring of vulnerable areas. GPS tracking monitors the location and movements of security personnel, ensuring compliance with patrol routes and responses to incidents.
4. Comprehensive access control
Simplified visitor management allows for easy tracking of facility access, documenting all entries and exits. Integration with access control systems helps efficiently manage employee and visitor credentials, so there’s less unauthorized access.
5. Data and analytics
Performance metrics track and analyze security operations, identifying areas for improvement. Data analysis helps find vulnerabilities and develop strategies to mitigate potential threats.
6. Compliance and documentation
These solutions aid in compliance tracking, helping make sure security operations meet regulatory requirements through documentation and reporting. Logs of security activities provide valuable audit trails.
Workforce management solutions from Trackforce provide the tools and capabilities necessary to build and maintain a unified security force, both physically and in the cyber world.
Plan for the future
Investing in an integrated security approach isn’t just about technology. It’s also about creating a culture of security awareness and resilience across all levels of an organization. As the digital and physical worlds merge, so do our strategies for protecting the sensitive data and systems that drive our operations.
Dive deeper into unified security strategies with our webinar,
Bridging Cyber & Physical Defenses: A Unified Approach to Securing Every Angle.
Learn from industry experts about:
- Identifying cross-domain vulnerabilities
- Training security teams for comprehensive protection
- Leveraging technology for enhanced security integration



