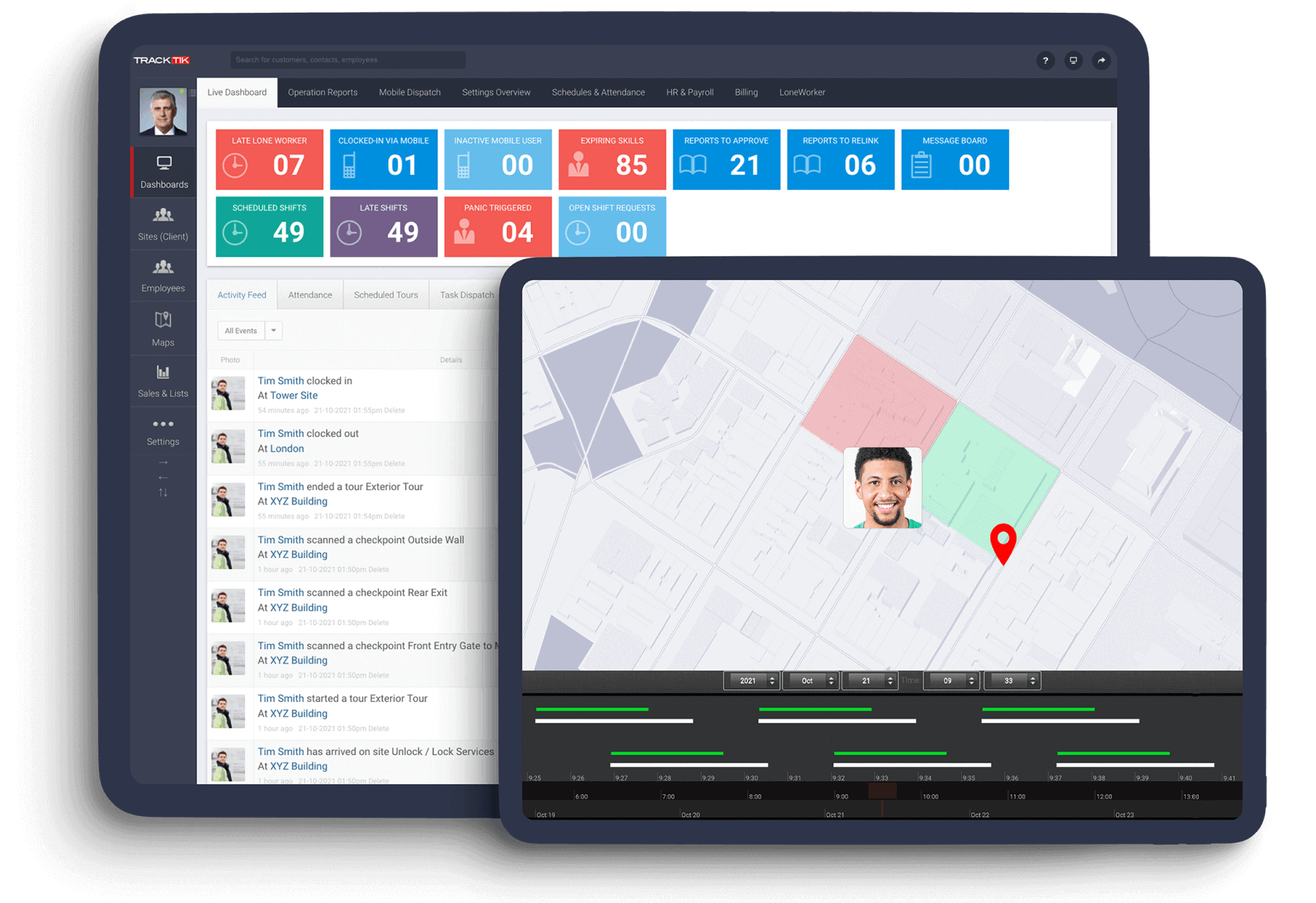
[ Resources ]
Blog Articles
Building a Security Operations Blueprint: Reducing Costs While Elevating Service Quality
Building a Security Operations Blueprint: Reducing Costs While Elevating Service Quality Talk to any security leader today,…
The Future of Physical Security Compliance: What HR, Legal, and Privacy Teams Must Prepare For (2026 and Beyond)
The Future of Physical Security Compliance: What HR, Legal, and Privacy Teams Must Prepare For (2026 and Beyond)…
When Security Teams Become Everything Teams
When Security Teams Become Everything Teams If you asked a security professional ten years ago to describe…
From Blind Spots to Benchmarks: How Manufacturers Are Closing the Safety and Compliance Gap with Smart Security Technology
From Blind Spots to Benchmarks: How Manufacturers Are Closing the Safety and Compliance Gap with Smart Security…
The Era of Unified Security Operations: Why Fragmented Tools Undermine Enterprise Risk Strategy
The Era of Unified Security Operations: Why Fragmented Tools Undermine Enterprise Risk Strategy Enterprise security has never…
From Warehouse to Final Mile: End‐to‐End Physical Security Strategies for Logistics Networks
From Warehouse to Final Mile: End‐to‐End Physical Security Strategies for Logistics Networks Complex transportation and logistics environments…
The Hidden Alliance Behind Safe Public Events
The Hidden Alliance Behind Safe Public Events When thousands gather for a political rally, parade, or festival,…
Beyond Pay Raises: The Surprising Retention Strategies Reducing Turnover by 50% in 2025
Beyond Pay Raises: The Surprising Retention Strategies Reducing Turnover by 50% in 2025 The physical security industry is facing…
Securing the Modern Data Center: Integrating Physical and Cyber Defenses
Securing the Modern Data Center: Integrating Physical and Cyber Defenses Data centers are at the heart of modern business…
The More We Automate Security, The More We Need Human Expertise
The More We Automate Security, The More We Need Human Expertise The physical security industry is experiencing a…
Checklist: Incident Reporting Essentials for Manufacturing Security Teams
Checklist: Incident Reporting Essentials for Manufacturing Security Teams In a fast-moving manufacturing environment, incident reporting is more…
The Hidden Cost of Non-Billable Overtime: A $1M Problem Hiding in Plain Sight
The Hidden Cost of Non-Billable Overtime: A $1M Problem Hiding in Plain Sight When it comes to…
The True Cost of Security Reporting Mistakes: How AI Transforms Documentation from Liability into Competitive Advantage
The True Cost of Security Reporting Mistakes: How AI Transforms Documentation from Liability into Competitive Advantage Security…
Why 79% of Security Teams Respond Faster – And Why It Matters”
Why 79% of Security Teams Respond Faster – And Why It Matters” The upcoming 2025 Physical Security…